Experience the Swiss Way to Cloud.
Built on enterprise-grade hardware, kvant is a highly automated, efficient, and sustainable Cloud solution, ensuring control over mission-critical workloads.
Rooted in the principles of open-source and entirely Swiss, from data center to application, kvant ensures scalability, flexibility, and unparalleled security.
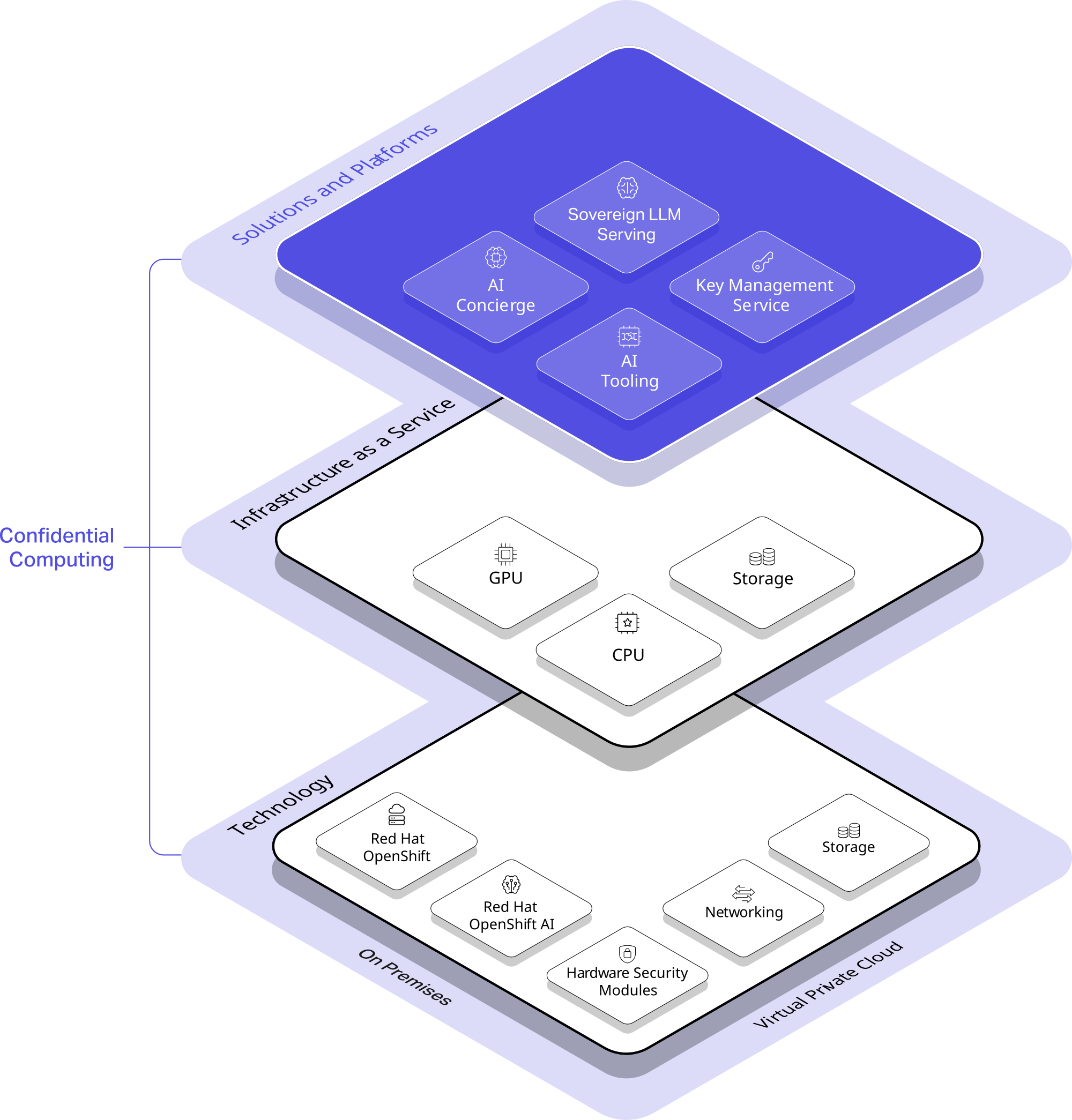
Solutions and Platforms
Solutions and Platforms empower enterprises to securely build, deploy, and manage AI applications within a sovereign cloud environment. From conversational AI and LLM hosting to advanced tooling and key management, kvant delivers end-to-end capabilities for compliant and scalable AI innovation.
Infrastructure as a Service
Infrastructure as a Service provides sovereign, high-performance infrastructure with scalable GPU, CPU, and NVMe storage resources. Designed for demanding workloads, it ensures security, reliability, and full control across compute and data layers.
Technology
kvant combines Red Hat OpenShift, HSMs, high-speed storage, and secure networking to deliver a powerful and compliant cloud-native foundation. It can be consumed flexibly—either on-premise or via Virtual Private Cloud—ensuring full sovereignty and control in any deployment model.
Solutions and Platforms
Infrastructure as a Service
Technology
Red Hat OpenShift
Red Hat OpenShift is a leading enterprise Kubernetes platform that enables the deployment, management, and scaling of containerized applications across hybrid and multi-cloud environments. Integrated with advanced security, developer tools, and automation, it streamlines application delivery while ensuring operational consistency and compliance.
Red Hat OpenShift AI
Red Hat OpenShift AI is an integrated platform for building, training, deploying, and managing AI models at scale within Kubernetes environments. It combines the flexibility of open-source tools with enterprise-grade security, automation, and lifecycle management for end-to-end AI workflows.
Hardware Security Modules
Hardware Security Modules (HSMs) are physical devices that securely generate, store, and manage cryptographic keys to protect sensitive data and digital assets. Integrated into Phoenix Technologies’ sovereign infrastructure, they ensure tamper-proof encryption operations, regulatory compliance, and full control over key usage.
Networking
Networking at Phoenix leverages Software Defined Networking (SDN) to isolate virtual data centers, manage traffic intelligently, and scale bandwidth up to 100 Gbps. This ensures secure, high-performance connectivity across cloud resources while maintaining full control and compliance.
Storage
Storage at Phoenix offers high-speed NVMe performance with built-in backups and snapshots for seamless scalability and data resilience. Distributed across four availability zones and featuring an air-gapped location, it ensures secure, sovereign data protection for critical workloads.
On Premises
kvant is also available as an on-premise solution, allowing you to deploy the full sovereign cloud and AI platform directly in your own data center. This setup ensures maximum control, security, and compliance—ideal for sensitive or regulated environments requiring air-gapped infrastructure.
Virtual Private Cloud
kvant Virtual Private Cloud (VPC) offers isolated, secure cloud environments tailored to individual organizations, ensuring full data separation and control. Built on sovereign infrastructure, each VPC provides dedicated compute, storage, and networking resources with support for confidential computing and regulatory compliance.
Confidential Computing
Our Confidential Computing approach transforms cloud security by safeguarding data at rest, in transit and in use. With encrypted enclaves, we ensure sensitive information remains confidential even in shared environments. This paradigm shift sets a new standard for secure data processing in the cloud.
Streamlining the Full Stack - from Data Center to Application.
Discover the Power of Hyperscaler Capabilities as we explore the seamless integration of OpenStack at scale. kvant opens the transformative potential of a virtual Public and Private Cloud, offering multi-tenancy, scalability, high availability, Infrastructure-as-Code, and Interoperability.
Entirely Swiss
With three availability zones strategically located in the region of Zurich, businesses benefit from a robust infrastructure that guarantees 99.99% uptime and higher.
Software Defined
The software-defined data center architecture empowers developers with granular control and automation capabilities. With exclusive access to Ansible scripts, developers can easily automate workflows and streamline operations.
Performance
kvant offers fully automated deployments for any type of workloads, enabling quick and seamless deployment processes.
Time to Market
kvant offers fully automated deployments for any type of workloads, enabling quick and seamless deployment processes. Complementary managed services further enhance efficiency and accelerate time to market for businesses.
Service
Expert Service Levels and guidance ensure comprehensive support throughout the deployment journey. Complementary managed services further enhance efficiency and accelerate time to market for businesses.
Cost Effectiveness
The platform embraces a truly open-source approach, eliminating unnecessary licenses so businesses can benefit from a cost-effective solution without hidden costs.
kvant is our innovative approach to cloud computing.
We focus on bringing you an innovative cloud platform and simplifying the onboarding process. We are committed to building a cloud for Switzerland, relying on local skills and resources, and prioritizing the principle of confidential computing. The journey to the cloud is a strategic move, and we are here to make it seamless and effective, ensuring you retain control of your mission-critical workloads.


